In the realm of enterprise applications, the firewall stands as a pivotal guardian against potential threats. This blog delves into a specific scenario where Sitecore support facilitated the implementation of Web Application Firewall (WAF) on Microsoft Azure for a Sitecore Managed Website. With WAF in place, access to the App Service was restricted solely to the Firewall’s IP, resulting in a 403 Forbidden error. The intricacies of pinpointing the exact rule causing this restriction within Azure Firewall are explored.

Simple Web Architecture:

The blog details a step-by-step process for identifying and addressing WAF rule blocks:
1: Accessing WAF Logs:
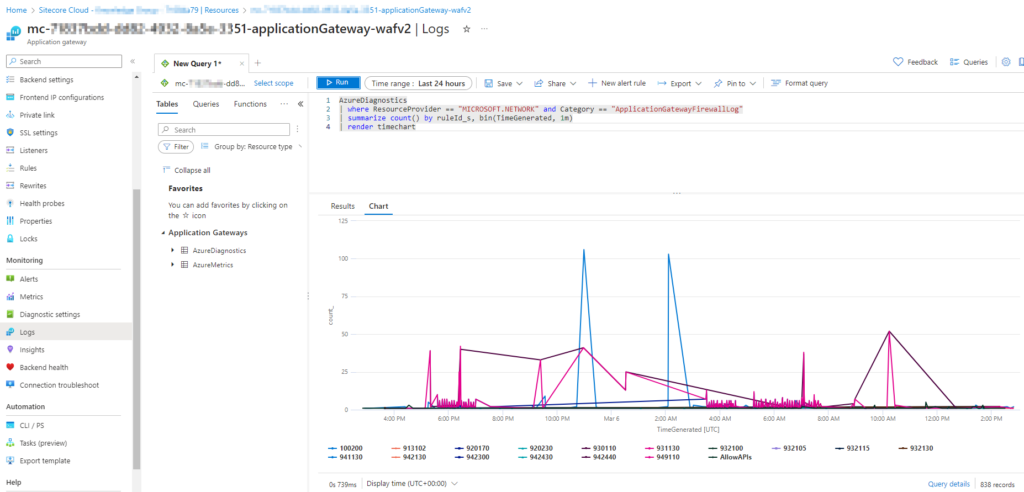
Navigate through the Application Gateway to access logs, running a following query in Azure Diagnostics to isolate rule-specific data.
AzureDiagnostics
| where ResourceProvider == "MICROSOFT.NETWORK" and Category == "ApplicationGatewayFirewallLog"
| summarize count() by ruleId_s, bin(TimeGenerated, 1m)
| render timechart2. Identifying Rule Numbers:
Hover over rules in the log to identify the rule numbers causing the issue, along with their occurrence frequency.
3. Disabling Rules in WAF Policy:
Move to the WAF Policy, locate Managed Rules, and selectively disable rules that might be blocking requests.
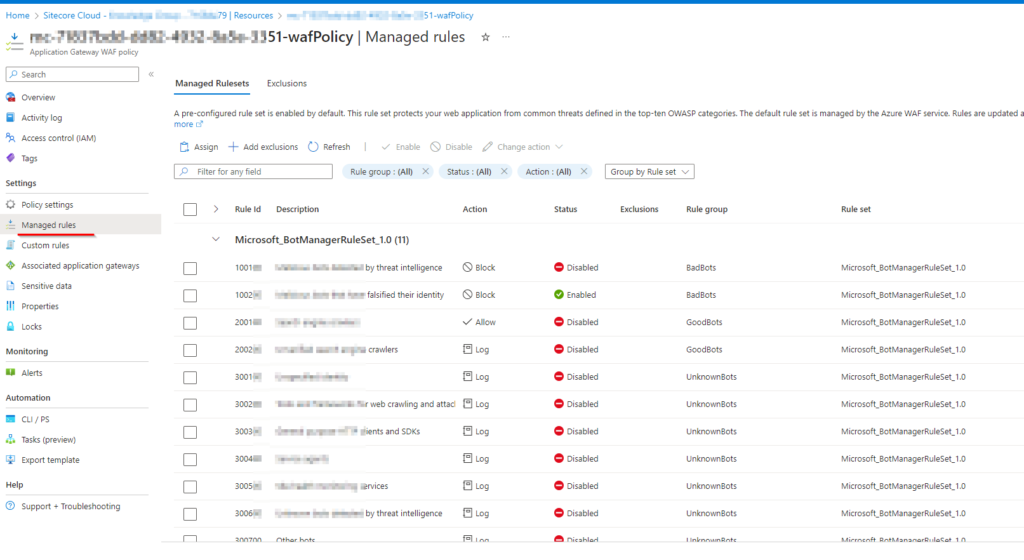
The firewall is designed to block certain requests as part of its intended function. The simplest approach is to deactivate the rule, but doing so leaves you susceptible to potential attacks that the disabled rule would otherwise prevent. The more intricate method involves addressing the application to ensure that requests no longer meet the rule conditions. It falls under your responsibility to handle these rules and determine whether their activation or deactivation is appropriate.
A heartfelt thank you to the Sitecore support team for their unwavering support. Happy securing!